Hacking Voice Assistants with Lasers
A team of cybersecurity researchers has discovered a clever technique to remotely inject inaudible and invisible commands into voice-controlled devices — all just by shining a laser at the targeted device instead of using spoken words.
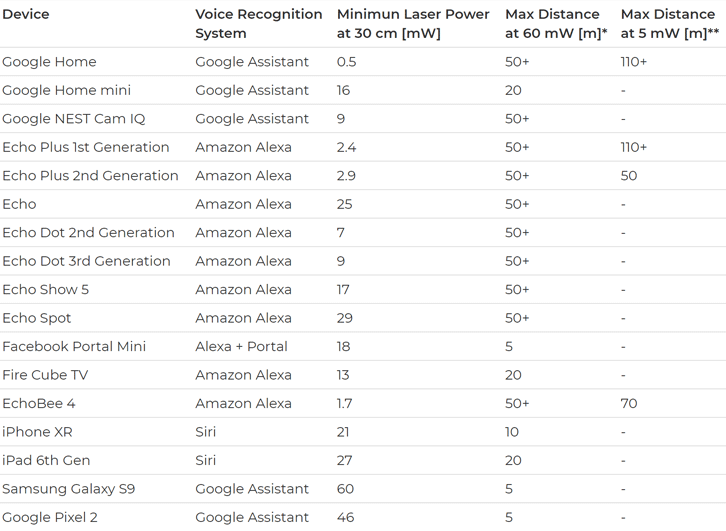
Dubbed 'Light Commands,' the hack relies on a vulnerability in MEMS microphones embedded in popular voice-controllable systems that unintentionally respond to light as if it were sound.
Smart voice assistants in your phones, tablets, and other smart devices, such as Google Home, Amazon Alexa, and Apple Siri devices, are all vulnerable to this new light-based signal injection attack.
Since the technique allows attackers to inject commands as a legitimate user, they can also hijack any digital smart systems attached to the targeted voice-controlled assistants. For example, attackers can:
- Control smart home switches,
- Open smart garage doors,
- Make online purchases,
- Remotely unlock and start certain vehicles,
- Open smart locks by stealthily brute-forcing the user's PIN number.
As shown in video demonstrations, researchers successfully opened a garage door by shooting a laser at a connected Google Home device, even from a separate building 230 feet away.
The maximum range for this attack depends upon the power of the laser and aiming capabilities. The attack can be mounted cheaply using a simple laser pointer, a laser driver, and a sound amplifier.
How To Protect Yourself
Software makers should offer users an additional layer of authentication before processing commands. For now, the best solution is to keep the line of sight of your voice assistant devices physically blocked from the outside and avoid giving them access to critical systems.

